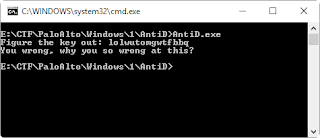
As someone who has participated in numerous Capture The Flag (CTF) competitions, I was excited when Huntress Lab announced their CTF late last year. Anytime a new organization ventures into hosting CTFs, it brings fresh perspectives, twists, and innovative approaches to data manipulation to obtain flags. I found their daily-released challenges to be particularly engaging. …
Huntress CTF 2023 – Unique Approaches to Fun Challenges