Busy under the pressure of releasing the new Dissecting the Hack book, the challenge went to the back of my mind until the 24th of July. I was facing a pretty hard-hitting bit of writer's block and frustration. I agreed to let myself have a break to do the challenge for one week before getting back to my commitments.
Although the challenge started in early July, it ran up until 15 September. There was an unspoken moratorium on answers/solutions while the challenge ran, but now that the samples are all freely available from their website, some are coming forth with how they completed them.
This is my story.
Challenge 1
The first challenge started out with downloading an executable from the flare-on.com website. I immediately threw it into IDA and started poking around, only to discover that it was just a dropper for the real challenge :) I let it do its thing, agreed to a EULA without reading it, and received the first challenge file:
File Name : Challenge1.exe File Size : 120,832 bytes MD5 : 66692c39aab3f8e7979b43f2a31c104f SHA1 : 5f7d1552383dc9de18758aa29c6b7e21ca172634 Fuzzy : 3072:vaL7nzo5UC2ShGACS3XzXl/ZPYHLy7argeZX:uUUC2SHjpurG Import Hash : f34d5f2d4577ed6d9ceec516c1f5a744 Compiled Time : Wed Jul 02 19:01:33 2014 UTC PE Sections (3) : Name Size MD5 .text 118,272 e4c64d5b55603ecef3562099317cad76 .rsrc 1,536 6adbd3818087d9be58766dccc3f5f2bd .reloc 512 34db3eafce34815286f13c2ea0e2da70 Magic : PE32 executable for MS Windows (GUI) Intel 80386 32-bit Mono/.Net assembly .NET Version : 2.0.0.0 SignSrch : offset num description [bits.endian.size] 0040df85 2875 libavcodec ff_mjpeg_val_ac_luminance [..162] 0040e05d 2876 libavcodec ff_mjpeg_val_ac_chrominance [..162]
Based on this output from the file, I can see first of all that it was built from .NET 2.0 (based on the mscorlib import). That'll be important later to determine what tool to analyze the file in; IDA Pro is not the most conducive tool for .NET applications.
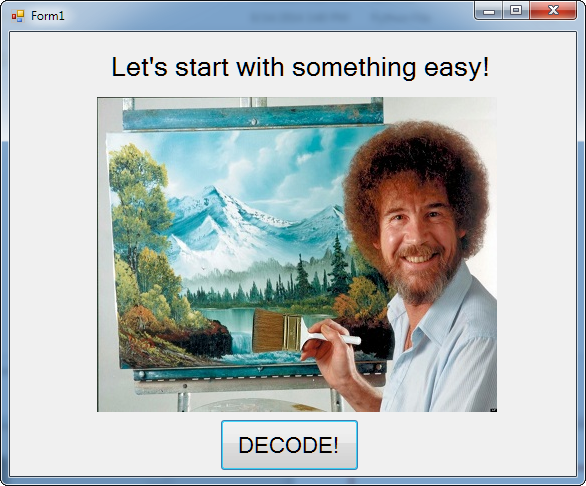
At this point, let's run it and see what happens:
The image shows some happy little trees and a great, big "DECODE" button. Clicking this button changes the image thusly:
Without any clue of what to do with the challenge, or what I'm actually looking for, I open it up for analysis with Red Gate .NET Reflector.